Reliable Access Control for Production Machinery
RFID System Enables a Convenient and Tiered Solution
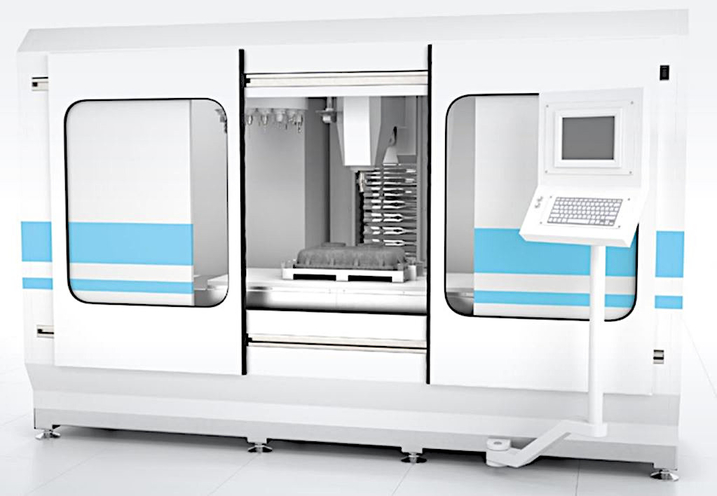
The Application
Modern production machinery is often a highly complex, highvalue investment. Operating personnel generally need to have certain professional qualifications and be specifically trained. These criteria are used to ensure occupational safety and health. In addition, they help protect the integrity of the machine and the process. Only qualified and authorized personnel may access the control panel of such machines for both regulatory and quality assurance reasons.
Another aspect that is becoming increasingly important is the documentation obligations. In addition to proving operational safety, detailed traceability of production steps is often required. An electronic logbook can be used to automatically record the machine parameters and the operator identity.
The Goal
Access to the machine should only be possible with an electronic “key” that uniquely identifies the authorized operator. This is to ensure qualified and safe operation of the machine and to prevent damage caused by operating errors. The intention is for access protection to be used to document operating times, parameter settings, and parts produced. The access concept needs to be quick, easy, and secure against circumvention.
The Solution

IPH-F61-V1 RFID read/write head
Employees with access rights receive an RFID tag, which is detected by an RFID read/write head on the machine. Several reading points can be set up on the machine to enable tiered approval of machine operation. The permitted operations can be broken down according to different access levels for operators, servicing personnel, and administrators. RFID tags in the form of key fobs are an ideal solution. Different colors can be used to visually identify different authorization levels. The tag features copy protection, which means its use can be instantly blocked if lost.
Technical Features:
IPH-F61-V1 RFID Read/Write Head
- Special flat design
- Connection cable with V1 plug (M12 x 1)
- IP67 rating
- Can be mounted on metal
- Connection to IDENTControl control interface
The Benefits

RFID tag used as a key
Reliable control of access to the machine is guaranteed. Authorized persons receive access immediately and without any complications. Operation and processes can be fully documented and tracked. The RFID tags used as keys are inexpensive, secure against circumvention, and difficult to copy. A single tag can be used to flexibly assign access authorizations for different machines on an individual basis. Time restrictions are easy to implement.
At a Glance
- Tiered access control
- High standard of safety
- Affordable tags with a high degree of copy protection
- System secure against circumvention
- Automated documentation possible
- High degree of protection for high-quality investment








 +45 7010 4210
+45 7010 4210